 |
Phishing refers to the act of sending emails that appear to be from reputable businesses, organizations, or authorities to deceive recipients into divulging sensitive information or providing resources. Phishing remains one of the most effective methods for hackers to scam individuals and infiltrate organizations by stealing credentials. You've likely encountered these emails in your inbox—they're very common. They might look like they come from a major bank or business you don't associate with, claiming an issue with your account needs immediate attention. Scammers often send these emails indiscriminately, hoping to "hook" a few recipients.
Types of Phishing Attacks
General Phishing: These are broad attempts where scammers send mass emails to as many people as possible. The goal is to catch a few unsuspecting individuals who will respond to the fake emails.
Spear Phishing: Spear phishing emails are more sophisticated and tailored to look like legitimate emails directed at a specific group. For example, an email might appear from a software vendor asking for login credentials to a cloud service, targeting a company's Human Resources staff. These attacks require significant research and planning but are more challenging to detect.
Whaling: Whaling targets high-level executives or people of authority within an organization. These emails are meticulously crafted to appear legitimate, hoping to trick these individuals into divulging highly valuable information.
Identifying Phishing Emails
Sender's Email Address: Carefully check the sender's email address. Scammers often create email addresses that closely resemble legitimate ones but with slight variations in spelling.
Subject Line: Phishing emails often have vaguely threatening subject lines, such as claiming there's a problem with your account that needs urgent attention or that you're in violation of some law. Conversely, they might offer enticing rewards to prompt quick action.
Greeting: Generic greetings like "Dear member" or "Valued customer" are common in mass phishing campaigns. However, spear phishing emails might include your name to appear more convincing.
Email Body:
- Spelling and Grammar: Look for errors in spelling and grammar. Although phishing emails have improved in this area, mistakes can still be a red flag.
- Content: Be wary of emails detailing account issues or offering prizes accompanied by instructions and links. Even if they look convincing with the right fonts, logos, and graphics, the email could still be fake.
Links: Phishing emails rely on tricking you into clicking on malicious links. Hover your cursor over the link (without clicking) to see the actual URL. Scammers often create URLs that closely mimic legitimate sites. Never click these links; manually navigate the website using a separate browser window.
Example of a Phishing E-mail:
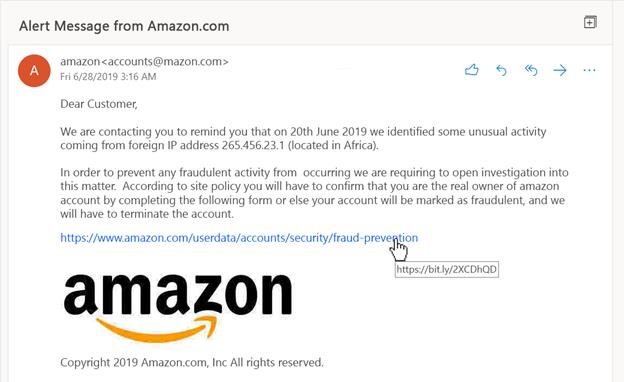
What to Do If You Suspect Phishing
If you suspect an email is a phishing attempt, delete it or block the
sender. Do not click links if you think the email might be legitimate. Instead,
open a new browser window and manually type in the website's address to log in.
Spam Emails
While sometimes less harmful than phishing attempts, spam emails can still
be annoying and potentially dangerous. Spam refers to unsolicited emails sent
in bulk, often for advertising, phishing, or spreading malware.
Tips for Handling Spam:
1. Use Spam Filters: Most email services offer filters that automatically route suspicious emails to a spam folder.
2. Avoid Unsubscribing: Clicking "unsubscribe" in spam emails can sometimes confirm to spammers that your email address is active, potentially increasing the spam you receive.
3. Be Cautious with Your Email Address: Avoid sharing your email address publicly and use different email addresses for other purposes (e.g., personal, work, online sign-ups).
4. Report Spam: Most email services allow you to report spam, which helps improve their filtering systems.
Conclusion
Phishing and spam are prevalent threats in today's digital world. You can
protect yourself and your organization from potential harm by staying vigilant
and recognizing the signs of malicious emails. Always exercise caution when
dealing with unsolicited emails and use reliable security practices to keep your
information safe.